My previous posts presented a brief history of physical security technologies, and the effect of the digital revolution <Link to part 2> on physical security. Today, we look at the challenge posed by the Internet of Things: making sense of digital data, specifically video data.
 Video Analytics
Video Analytics
The intensive penetration of video surveillance cameras created a new challenge. Having made huge investments made in purchasing and installing cameras in the field, it is the industry recognized it was almost impossible to monitor all the cameras 24/7. Therefore, there arose a need for a method to assist in deciding when an activity at any specific camera was important enough to record or to issue an alarm. This need was the trigger for Video Analytics (also called Video Content Analysis – VCA) technology.
VCA offers a variety of software algorithms capable of detecting multiple events, from simple video motion detection (VMD), through left object or taken object detection, License Plate Recognition (LPR), Facial Recognition, loitering detection, congregation detection and other types of behavior detection.
All these valuable capabilities became possible not only inside the protected premise, but also outside of the perimeter, enabling an earlier and wider security circle.
VCA technology is a teenager now, meaning it has only achieved a fraction of its potential. Unlike in the past, the new generation of VCA products does not require setup by experts and is capable of alarming upon events and sequences spanning multiple cameras.
Mobile and Wearable
The smartphone, which changed our life — for better or worse — during the recent decade, has changed the security world as well. The ability to view video and other information anywhere, enables security personnel to manage events even while away from the scene location. Furthermore, the smartphone camera enables anyone – whether first responders or civilians – to transmit live video, audio, GPS location and more from the event scene.
 During the recent few years, body-worn cameras (also called Bodycam or Police Cameras) began penetrating the law enforcement and first responders sectors. Although the original motivations for these cameras was for evidence purposes and to reduce officer liability during events, these are now being used as real-time cameras for event management and as a sophisticated sensor in the field for purposes such as suspect license plate recognition or suspect facial recognition.
During the recent few years, body-worn cameras (also called Bodycam or Police Cameras) began penetrating the law enforcement and first responders sectors. Although the original motivations for these cameras was for evidence purposes and to reduce officer liability during events, these are now being used as real-time cameras for event management and as a sophisticated sensor in the field for purposes such as suspect license plate recognition or suspect facial recognition.
C4I and VMS systems had started supporting smartphone display, smartphone camera and body worn cameras.
Other wearable sensors are available and providing a variety of alarms from the field such as smoke or hazardous gases, fall detection, virtual tripwire and more. Weapon-installed sensors provide alarms upon any weapon activity such as pullout, trigger on and shooting.
Mobile and wearable technologies create a new reality, in which most cameras and sensors worldwide are mobile rather than fixed. For the sake of comparison: about 350 million video surveillance cameras were deployed over the past five decades, while within a single decade, several billion smartphones have been sold.
PSIM
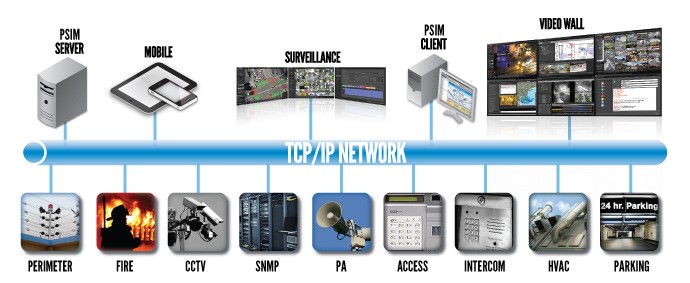 The variety and lack of interoperability of security systems poses a major problem in the market, requiring expensive integrations to connect components and systems to one another. In order to overcome this issue, a new concept of a unified protocol connecting all systems has been introduced under the name Physical Security Information Management or PSIM.
The variety and lack of interoperability of security systems poses a major problem in the market, requiring expensive integrations to connect components and systems to one another. In order to overcome this issue, a new concept of a unified protocol connecting all systems has been introduced under the name Physical Security Information Management or PSIM.
PSIM software enables managing systems and components made by differing vendors by a single application as well as ‘plug-and-play’ connection of any camera or sensor to any VMD or C4I.
PSIM provides multiple functions: Sensor data collection, data analysis and real situation identification, quick event verification, step-by-step operating instructions, event reporting to predefined users and operators performance monitoring.
Furthermore, PSIM is not limited to security systems but can rather integrate building management systems, fire alarm systems and more.
The leading PSIM standards are ONVIF and PSIA. To date, most of the leading security vendors offer compatible products.
In my next post, we’ll discuss what lies ahead for Physical Security in the coming years.


 Digital Video
Digital Video During the 90’s, digital video transmission and storage technologies spread rapidly throughout the physical security market. The old, cumbersome and unreliable VCRs were replaced by new, maintenance-free Digital Video Recorders (DVRs), which enabled immediate access to any video footage. Analog video transmission over coaxial cable was taken over by digital video, which enabled sharing and distribution to multiple users at multiple locations.
During the 90’s, digital video transmission and storage technologies spread rapidly throughout the physical security market. The old, cumbersome and unreliable VCRs were replaced by new, maintenance-free Digital Video Recorders (DVRs), which enabled immediate access to any video footage. Analog video transmission over coaxial cable was taken over by digital video, which enabled sharing and distribution to multiple users at multiple locations.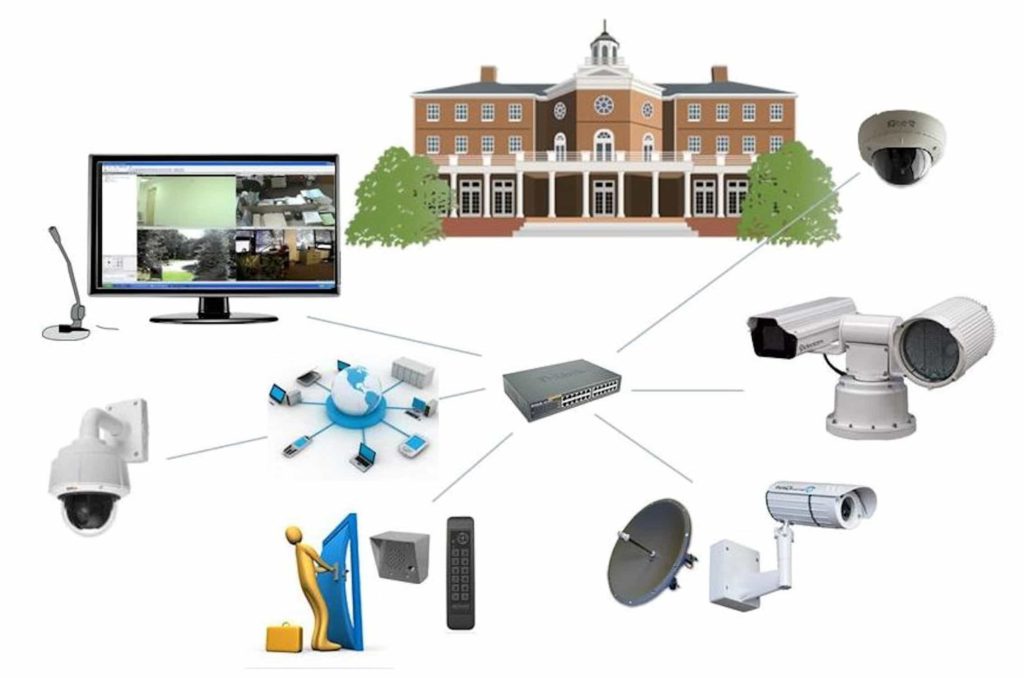 At the rise of the millennium, along with the establishment of IP technology as a leading communication standard and widespread usage of IP network at any house and business, video-over-IP solutions were introduced. These included video encoders, which compressed analog video input to digital video over IP networks, and IP cameras with on-board IP ports.
At the rise of the millennium, along with the establishment of IP technology as a leading communication standard and widespread usage of IP network at any house and business, video-over-IP solutions were introduced. These included video encoders, which compressed analog video input to digital video over IP networks, and IP cameras with on-board IP ports.
 9-11
9-11
 The physical security market has experienced some significant changes during the recent decades. Whereas once physical security was based solely on guards, fences and gates, the story of the physical security market has been rewritten by technological development and a change in the type of threats we face.
The physical security market has experienced some significant changes during the recent decades. Whereas once physical security was based solely on guards, fences and gates, the story of the physical security market has been rewritten by technological development and a change in the type of threats we face. During the 70’s, intruder detection alarm systems were introduced. These systems were the enabler for rapid growth of the central alarm monitoring service, providing security solutions 24/7 for the residential and enterprise markets.
During the 70’s, intruder detection alarm systems were introduced. These systems were the enabler for rapid growth of the central alarm monitoring service, providing security solutions 24/7 for the residential and enterprise markets. Despite the high cost, low video quality and difficulty to access video footage of a specific event, these CCTV systems generated a real revolution in the security market and upgraded the security level. Eventually, the return on investment model was proven by a reduction of manpower and lower false alarm costs.
Despite the high cost, low video quality and difficulty to access video footage of a specific event, these CCTV systems generated a real revolution in the security market and upgraded the security level. Eventually, the return on investment model was proven by a reduction of manpower and lower false alarm costs.